
DORA Introduction
Full name : Digital Operational Resilience Act (DORA)
Origin: European Union Regulation
Objective : To strengthen the digital resilience of financial institutions in Europe.
Sectors affected : Banks, insurance companies, asset managers and other financial institutions.
Effective date: 17 January 2025
DORA’s impact on banks and insurance companies like AG
DORA aims to protect the financial sector's digital infrastructure, ensuring that essential financial services remain accessible if faced with undesirable incidents (cyberattacks, etc.).
With this aim in mind, the DORA Regulation requires financial institutions to:
- Establish a solid system for managing digital risks
- Implement mandatory incident reporting systems
- Adhere to strict digital resilience testing protocols to enhance cybersecurity and ensure recovery from cyber threats and operational issues.
The DORA law also requires to:
- Provide greater transparency towards the regulatory bodies
- Share identified threats
- Collaborate closely with counterparts in the sector
- Focus more on supplier risk management
In other words, AG will now be responsible for the digital resilience of the entire supply chain.
How did AG prepare for DORA compliance?
For detailed information on AG’s roadmap to DORA compliance, we consulted Francis De Cock (IT DXO) and Inge De Decker (Operational Risk Management), who shared their insights.
We began by explaining the compliance requirements to our Chief Information & Technology Officer, Philippe Van Belle, and AG's Chief Risk Officer, Nathalie Vanderbecken, who consequently supported the project launch.
The first step was to create a centralised project management team, which drew up a roadmap and schedule based on the DORA priorities.
The second stage involved setting up a multi-disciplinary team by pillar to oversee compliance efforts.
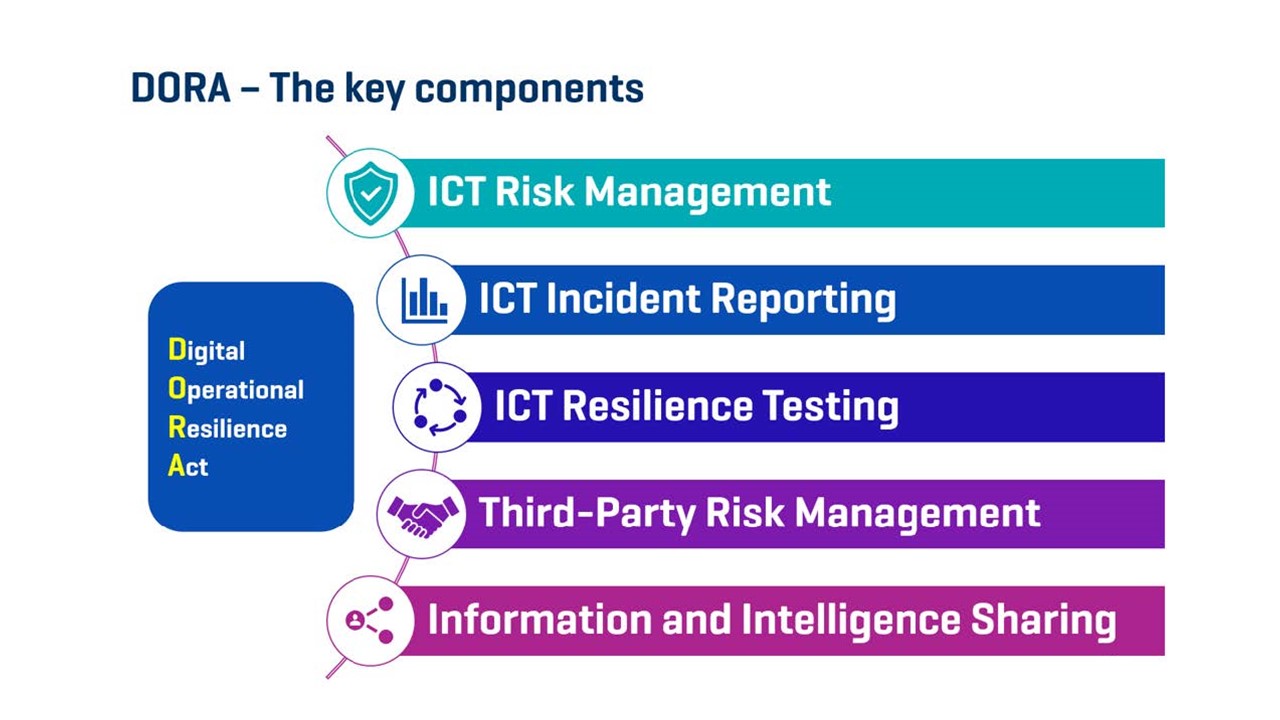
The first pillar outlines the risk management policies that financial institutions must implement. What does this specifically mean for AG?
The second pillar of DORA relates to reporting. In particular, it stipulates that it is essential for financial institutions to immediately report any major incident to the National Bank of Belgium.

The third pillar requires robust preventive mechanisms to ensure that financial institutions can withstand and recover from IT disruptions without affecting their operations.
It’s basically the pillar of resilience – based on two principles.
The first principle focuses on operational resilience. As part of this, we have put in place advanced technological infrastructure, including the duplication of data centres. This configuration ensures continuous availability of services, with one centre able to seamlessly take over operations if the other encounters problems. In this way, we ensure uninterrupted service delivery and maintain our customers' trust. We also have our SOC (Security Operation Centre), which monitors, detects and responds to potential threats in real time to protect our infrastructure.
The second principle is based on Threat-Led Penetration Testing (TLPT). Results are meticulously reported to the regulatory bodies to ensure transparency and compliance with DORA's strict standards.
The fourth pillar requires financial institutions to ensure that their IT service providers are carefully selected and monitored.
The fifth and final pillar relates to information sharing between peers in the event of a cyber threat.
DORA strongly encourages the exchange of information and intelligence on cyber threats within trusted communities of financial entities. This may include indicators of compromise, tactics, detection techniques, response procedures, mitigation strategies and cyber security alerts. The aim remains the same: to raise awareness of cyber threats and strengthen defence capabilities in the financial sector.
Looking back at the journey towards DORA compliance
Reflecting on our initial steps towards compliance, we have identified six key success factors.
1. Preparing and planning early: Preparation is crucial. It was essential to start preparing for DORA compliance well in advance of the deadlines, especially given the extensive regulatory documentation. This enabled us to fully understand the requirements, evaluate the current systems and identify any necessary changes or improvements.
2. Training multi-disciplinary teams: Compliance with multi-faceted regulations necessitates multi-disciplinary teams comprising professionals from various departments, such as IT, cyber experts, the Cloud centre of excellence, risk and business continuity management, procurement and IT operations, to ensure a holistic approach to the regulatory challenges.
3. Utilizing existing frameworks: Leveraging existing qualifications and frameworks proved advantageous. We were lucky enough not to have to start from scratch. Our prior compliance with the ISO 27001 standard has enabled us to meet numerous regulatory requirements. Existing certifications provided a solid foundation for compliance with the DORA law.
4. Engaging with management: It is essential to ensure that management is fully engaged and supportive of DORA compliance initiatives. Management’s backing not only facilitates resource mobilisation but also reinforces the cultural change that has already been set in motion through our previous achievements, such as ISO certification, bringing us close to our compliance targets
5. Documenting and reporting: It is recommended to maintain detailed and accurate documentation of all compliance processes, tests and incidents. This documentation is essential for internal reviews and audits, as well as for demonstrating compliance to regulatory bodies.
6. Staying informed and agile: The security landscape may continue to evolve over the coming months. Organisations must stay abreast of updates and be prepared to adapt their strategies and processes accordingly. The regulatory landscape can also change, so staying informed ensures ongoing compliance.
